In today’s digital world, cloud storage has become an essential part of many people’s lives and businesses. Whether you’re saving your photos or your company’s most sensitive data, the cloud is a convenient and efficient place to store files. However, with great convenience comes great responsibility.
Protecting your data from unauthorized access is vital. One of the most effective ways to secure your cloud storage is by using end-to-end encryption (E2EE). In this article, we will guide you through the process of implementing end-to-end encryption in cloud storage, ensuring your data remains private and secure.
Table of Contents
What Is End-to-End Encryption in Cloud Storage?
End-to-end encryption in cloud storage ensures that only the sender and the recipient can read the files being exchanged. This means that even the cloud service provider cannot access the data stored in your cloud account. When data is encrypted end-to-end, it is transformed into a secure format using a cryptographic key that only you (or the intended recipient) can decrypt.
This is in contrast to traditional encryption models, where data is decrypted on the cloud service provider’s servers before being passed on to you. With E2EE, your data is encrypted on your device, transferred in its encrypted form, and only decrypted once it reaches its final destination—your device or the device of someone you’re sharing with.
Why Is End-to-End Encryption Important?
End-to-end encryption is crucial because it minimizes the risk of unauthorized access. Data stored in the cloud can be vulnerable if not properly encrypted. Without E2EE, hackers or even cloud service providers could potentially access your data. With the increasing number of data breaches and cyberattacks, implementing end-to-end encryption has become more crucial than ever to protect sensitive information, including financial records, personal documents, and private messages.
Did you know that in 2020 alone, the number of data breaches increased by 141%? According to the 2021 Identity Theft Resource Center report, 1,291 data breaches were reported in the first half of the year alone. This statistic underscores the importance of securing your data, particularly when utilizing cloud storage.
How Does End-to-End Encryption Work?
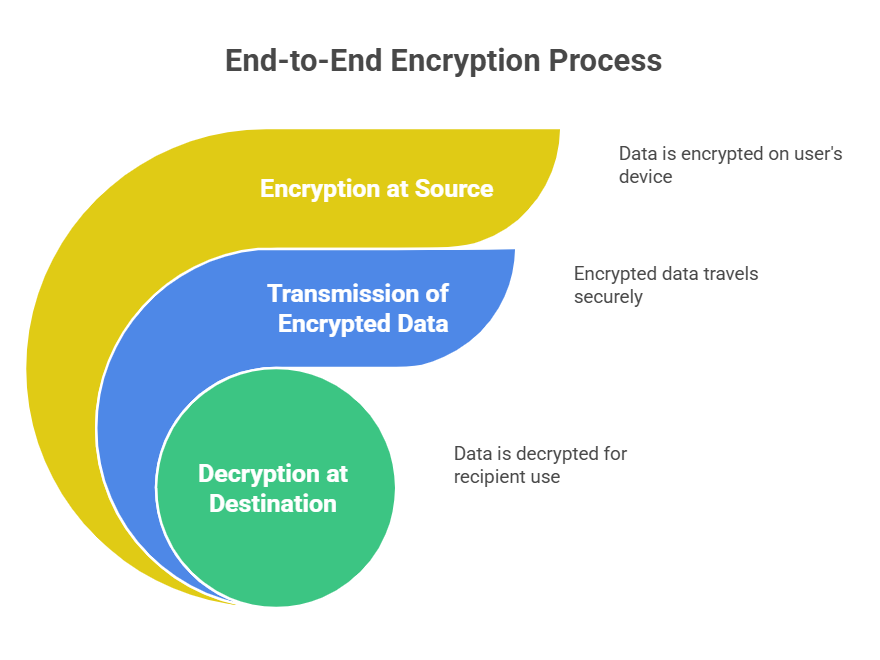
Here’s a simple breakdown of how end-to-end encryption works:
- Data is encrypted at the Source: When you upload a file to cloud storage, it gets encrypted on your device (computer or smartphone). This encryption uses a secret key, which is unique to you.
- Encrypted Data is Transmitted: Once encrypted, the data is sent over the internet. Even if hackers intercept the transmission, they will only see the encrypted data. Without the decryption key, they won’t be able to read it.
- Decryption at the Destination: When the file reaches its intended recipient or your device, the data is decrypted using the secret key. The recipient can only decrypt it if they have the correct decryption key.
Note: End-to-end encryption is only as secure as the secret key it uses. If someone else obtains the key, they can also decrypt the data. So, it’s essential to store your decryption key safely.
How Can You Implement End-to-End Encryption in Cloud Storage?
Now that we understand the importance of E2EE, let’s look at how you can implement it in cloud storage.
Choose a Cloud Storage Provider that Supports End-to-End Encryption
Not all cloud storage services offer end-to-end encryption by default. Therefore, the first step is to choose a service that supports it. Some popular cloud storage providers that provide E2EE include:
- Tresorit: Known for its robust security features and end-to-end encryption (E2EE), Tresorit is ideal for both businesses and individuals.
- Sync.com: This provider offers seamless integration with end-to-end encryption for easy file sharing and storage.
- ProtonDrive: ProtonDrive, offered by ProtonMail, is another service that provides E2EE for cloud storage, with a strong focus on privacy.
Tip: When choosing a cloud storage provider, ensure that you verify whether they manage the encryption keys or if you retain control. Retaining control is crucial for higher privacy and security.
Encrypt Your Files Before Uploading
If your cloud storage provider doesn’t offer end-to-end encryption, you can still implement it by encrypting your files before uploading them. Here’s how:
- Use Encryption Software: Software like VeraCrypt or AxCrypt allows you to encrypt individual files or entire folders. These tools provide strong encryption algorithms to protect your data.
- Upload the Encrypted Files: After encryption, upload the encrypted files to your cloud storage. The cloud provider will store the encrypted version of your files, and only you (with the correct decryption key) can decrypt them.
- Accessing Encrypted Files: To access encrypted files, download them from the cloud and decrypt them using the provided decryption key.
Example: I’ve used VeraCrypt to secure sensitive files and upload them to my cloud storage. It gives me peace of mind knowing that even if someone accesses my cloud, they won’t be able to read the files without the decryption key.
Use Strong Encryption Algorithms
For maximum security, always use strong encryption algorithms. The most commonly recommended encryption standards are:
- AES-256: This is one of the strongest encryption standards available today. It’s widely used for both personal and business encryption.
- RSA: RSA encryption is often used for securing the transmission of the encryption key.
Most encryption software and cloud storage services support these algorithms.
Did you know that government agencies and financial institutions use AES-256 to secure highly sensitive data?
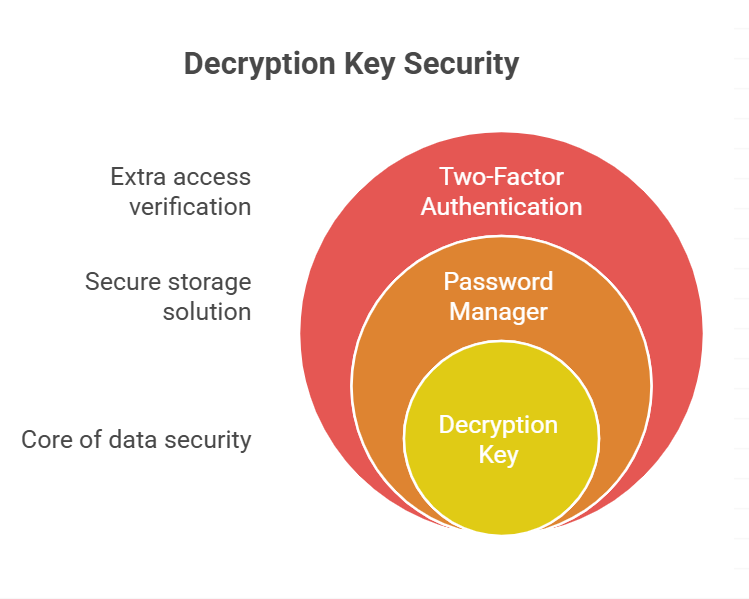
Keep Your Decryption Key Safe
As mentioned earlier, end-to-end encryption is only as secure as the decryption key. If you lose your key or it gets compromised, your data is no longer safe. Here are some best practices for keeping your decryption key safe:
- Use a Password Manager: Password managers like 1Password or Bitwarden can securely store your decryption key and other passwords.
- Two-Factor Authentication (2FA): Enabling 2FA adds an extra layer of security by requiring both your password and a second form of verification (like a code sent to your phone) to access the decryption key.
Frequently Asked Questions (FAQs)
1. Is end-to-end encryption 100% foolproof?
No, while end-to-end encryption offers a high level of security, it is not entirely foolproof. The security of E2EE depends on factors like the strength of the encryption algorithm, the security of your decryption key, and the security practices of the cloud storage provider.
2. Can cloud service providers access my encrypted files?
With end-to-end encryption, cloud providers cannot access your encrypted files. The files remain encrypted on the server, and only you (or the recipient) can decrypt them with the decryption key.
3. Do I need to encrypt every file before uploading to the cloud?
If your cloud storage service offers end-to-end encryption, you don’t need to encrypt files manually. However, if you’re using a provider that doesn’t provide E2EE, you should encrypt files before uploading them.
4. What happens if I lose my decryption key?
If you lose your decryption key, you will not be able to access your encrypted files. Therefore, it’s important to keep a backup of your decryption key in a secure location, such as a password manager.
Conclusion
Implementing end-to-end encryption in cloud storage is a crucial step toward protecting your data. By selecting a service that supports E2EE, utilizes strong encryption algorithms, and safeguards your decryption key, you can ensure that your files remain private and secure from hackers or unauthorized access. Whether you’re an individual looking to secure personal files or a business aiming to protect sensitive client data, end-to-end encryption is the key to achieving peace of mind in the cloud.
Remember: The world of digital security is ever-evolving. Stay informed and always ensure you’re using best practices to protect your data. Have you already implemented end-to-end encryption (E2EE) in your cloud storage? If not, do you think it’s something you’ll consider doing for extra security?
This post contains affiliate links. I may earn a commission if you make a purchase through them, at no extra cost to you.








